OSCP: Try harder and try smarter!
Hello world! I’ve recently passed the OSCP. In this post I’ll try to share the learning material which helped me pass. Most of these things are not mentioned in the syllabus but turned out to be essential. I collected many bookmarks while preparing for the OSCP but to be honest I only used a fraction of them. So, here are the ones I appreciated the most.
Happy Hacking!
Read this before signing up:
These two article series will give an overview of what the OSCP is about and if the topics are interesting for you.
Read the section about the Exam.
Resources for working in the lab:
This is my go-to resource when stumbling on a new service. The gitbook is well-structured and holds most of the topics you need in the lab.
The PayloadsAllTheThings repository has plenty of tips and tricks. Bypassing SQLi payloads, reverse shells, privilege escalation and a lot more.
In my opinion, the one and only script necessary for privilege escalation enumeration.
Linux and Windows binaries to bypass security restrictions.
Pre-compiled kernel exploits for privilege escalation.
Practical preparation:
Even though the PWK labs are great, there are many free labs to train your skills.
This is a great training place for all web security related things. For the exam preparation I would suggest doing at least the command injection and SQL injection exercises.
The Buffer Overflow are 25 points in the exam. I would really make sure to prepare properly and get these points within a short time. The TryHackMe lab is the perfect place for this. You got more than ten vulnerable binaries where you can improve your skills.
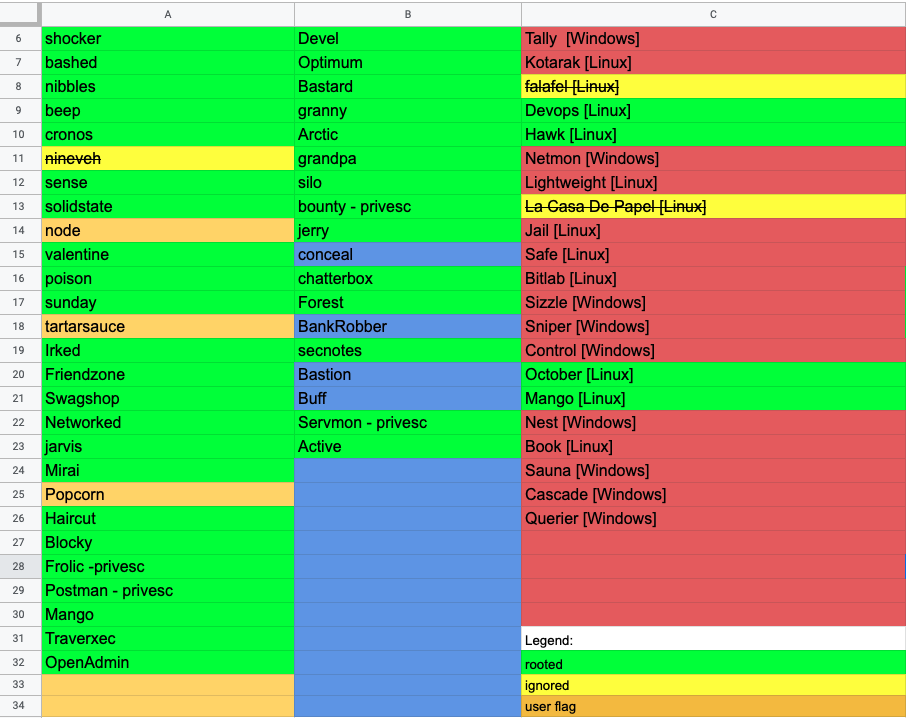
I started working on the list after my lab expired. Being able to solve some easy and medium machines is a self-control mechanism to check if you are ready to pass the exam.
Knowledge persistence:
One of the most important things while practicing in the lab is taking notes. I started with classical solutions like OneNote and Joplin but these notebooks became a complete mess in no time. Because of this I started using Xmind. With Joplin for taking notes while working on the machines and Xmind for noting every command used I could work most efficiently. Retrospectively, using Xmind and Joplin is a practical example for the separation of concerns.
This is the Mindmap I created while preparing for the Exam.
Tips and tricks:
- Restart the machine before debugging the exploit!
- Create your own cheatsheet.
- Email
proctoring@offensive-security.coma few days before your exam to get a test proctoring session.
HackTheBox Status: